Avoiding Ads Everywhere With Wireguard VPN and Pi-Hole
Ads are evil.
Yes, there’s an argument to be made for they’re a necessary evil to keep the internet (with all its content) afloat. But so many ads are just horrible - they slow down your web browsing, and they track your movements across the internet.
This is a feature, not a bug. The modern internet has real-time ads. When a visitor comes to a site, a bunch of companies will get information on the new visitor. Bots will then bid for ad space on that page the user is currently visiting as it is loading for the user.
This entire process means the ad companies need to harvest data about you. Zappos might not want to advertise to you, unless you have a history of buying shoes online. That data, your previous browsing habits, is required for the real-time ad markets to function (as well as being lucrative for other, non-ad purposes), so people have an interest in getting it.
Ad blockers are a simple, effective solution - they speed up your browsing (by allowing pages to load without all those ads from third-party servers) and they protect your privacy (by blocking the various tracking websites that build data on you). But they have a limitation - most ad blockers only work at the browsers level - they can’t defend you from ads within applications (either on phone or on PC), nor on locked-down devices, like game consoles.
Enter Pi-Hole
Pi-Hole is a network-level, DNS (Domain Name System) ad blocker.
Ok, what does that mean?
We’ve talked about DNS before on this blog, but as a quick refresher, when you enter in the name of a website (like seanzwrites.com), your computer does a DNS lookup to translate that human-readable address to the numerical IP address of the site.
The Pi-Hole acts as a DNS server on your home network, resolving your computer’s DNS lookups (and those of other devices on your network). But, when your computer asks for an known ad service (like doubleclick), the Pi-Hole simply responds that it couldn’t find it, so the ad is never loaded, the page loads faster, and the ad tracking networks don’t receive as much information about your browsing.
To be clear, ad networks have plenty of ways of getting your browsing data, but we’re at least stopping one of them.
While the Pi-Hole might not be as effective at blocking ads in browser as your friendly browser plugin, it can defend every device on your home network from ads, in every app.
That’s important - that means it blocks ads:
- On your phone (including inside apps)
- On your gaming console
- On all applications on your computer
Better still, it comes with a really nice, friendly, website where you can view detailed statics about your internet, so if you wanted to know how much data your internet-connected toaster was sending back to the manufacturer, it will happily show that to you.
While you can technically run the Pi-Hole software on any device, you’ll probably want to run it on a Raspberry Pi - the $35 computer. The pi is cheap, small, silent, and consumes a fraction of the power your desktop does, which are all important attributes as the Pi-Hole needs to be running 24/7.
OK - so assuming I’ve sold you on the power of network-level ad blocking, here’s an excellent tutorial at Motherboard on how to setup a Raspberry Pi with Pi-Hole.
One small caveat for advanced users (newbies please disregard) - you don’t
actually need a mouse/keyboard/monitor to setup your Raspberry Pi - if you are
comfortable with using SSH already, just place a file called ssh on the SD
card root
directory. Once
you boot the pi, you can ssh in with with username pi and the password
raspberry.
OK - once you’ve followed that tutorial, you hopefully banished ads from your home, and there was much rejoicing.
…But what about when you’re not at home?
Wireguard
You’ve setup your Raspberry Pi, you’ve declared victory against the ads in your house, but you probably go outside sometimes (or, at least, you used to, in the ‘Before COVID’ time). Wouldn’t it be great if you could have your Pi-Hole shielding you from ads when you’re riding the bus, or in a coffee shop?
You can. We’re going to setup a home VPN (Virtual Private Network). This will allow us to take advantage of our Pi-Hole setup wherever we are.
Unlike a commercial VPN (something like NordVPN, Private Internet Access, etc), which is often used for hiding your web browsing history from your ISP, our home VPN will act more like a corporate VPN - enabling us to access resources on our home network (in this case, the Pi-Hole) while we’re traveling and not connected to our home network.
Home VPNs have several nifty uses, like limiting how many devices are exposed to the internet. For example, internet-connected webcams are a mess to secure - there were several articles on how burglars have been exploiting internet-connected cameras to know when you’re not home. Placing the cameras on your home VPN enables you to still access them remotely, without exposing them to the dangers of the open internet.
However, we’re going to be talking about connecting devices to the Pi-Hole. By connecting to your VPN at home, which is protected by a Pi-Hole, your devices on the VPN will have access to the same ad-blocking protection, wherever they are.
To do this, we’re going to setup a Wireguard VPN server on the same Raspberry Pi that’s running the Pi-Hole software, that will let us connect to our home network wherever we are.
Ok, time for a technical aside.
There are several VPN technologies out there. The ‘good’ ones are OpenVPN, IKEv2/IPSec, and Wireguard.
Wireguard is the youngest of the three. However, it’s incredibly-well regarded, it’s faster than the other two, and it’s far easier to setup, so it’s what I’ll be talking about in this article. But, you’re probably fine with any of the three. As long as you don’t use PP2P or L2TP (which are very old and have security/performance concerns), you’re likely safe.
If you need a VPN protocol that works without installing any software on your PC, go with IKEv2/IPSec instead. There’s an excellent tutorial on setting up StrongSwan (the open source IKEv2/IPSec) implementation, and you can easily do this on your Raspberry Pi.
While it’s not really applicable to our home-VPN discussion, you should never use custom-made VPN protocols (like a special app provided by a commercial VPN provider). If you are using a commercial VPN, if they’re reputable, they will give you an option to use OpenVPN or IKEv2/IPSec or Wireguard to connect to their network.
A Home Of Our Own
Before I give you the Wireguard tutorial links, we’ll need to setup a domain for ourselves. Remember, computers on the internet talk to each other using numerical IP addresses, not friendly names. And, if you’re on normal residential internet, your home IP address likely changes every so often.
To solve this, we’re going to grab ourselves a domain name, something that we can point to our home internet address, and update when our IP address changes.
While you could pay for an actual domain (like I do for this site), since all we need is an address to point to our home IP, we’ll use a free DNS service - Afraid.org.
Afraid.org will offer us a free subdomain - so instead of getting seanzwrites.com,
you’ll get seanvpn.[one of their provided domains].org. They’ll also give us a
script we can run to keep our home address, and their record, in sync.
Afraid.org’s documentation, while functional, assumes some existing knowledge you might not have. Instead, I’d take a look at this excellent tutorial on using their free DNS service. Once you’re setup, you’ll have an internet name that you can use to connect to your VPN from anywhere.
Getting Our VPN Up And Running
Alright, we’ve got our ad blocker, we’ve got our public internet name, we’re ready.
I’m going to point you to two tutorials - both are excellent, but they offer different levels of detail. Try one, and if it doesn’t work for you, or if you get stuck, try the other!
Note: In the Sigmdel tutorial, in step 4.1, the tutorial references some scripts that are a bit dated. They still work, but you may need to tweak them for your needs.
Getting Wireguard Devices to Use Pi-Hole
Ok - you’ve likely finished the tutorial… and you still have ads. Don’t panic, that’s expected.
We’ll need to make two final changes, just two things before we’re add free!
First, we’ll need to tell the Pi-Hole to allow connections from the Wireguard VPN. To do this, go to http://pi.hole from a computer on your home network - this is the Pi-Hole admin interface.
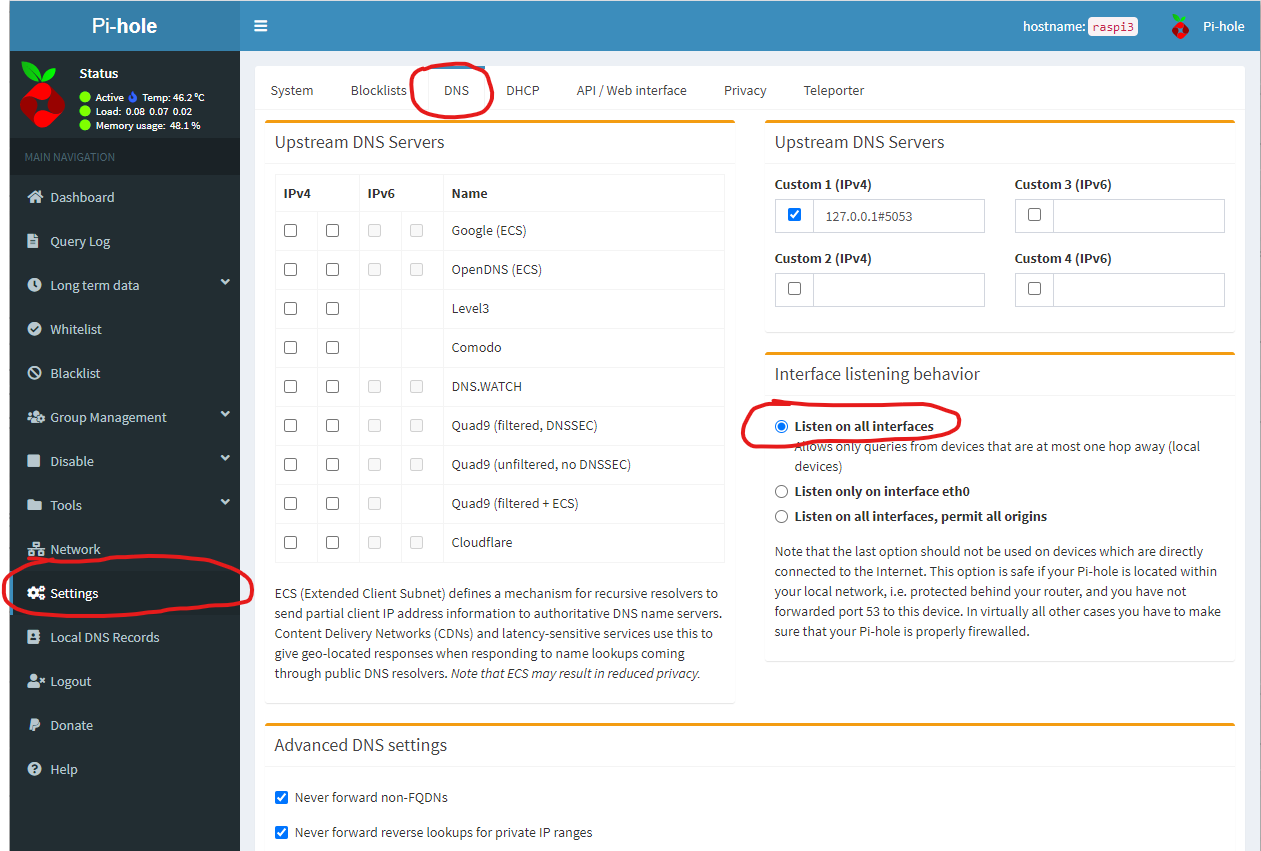
Once you’ve logged in - you just have four clicks:
- Click on ‘Settings’ on the panel on the left.
- Click ‘DNS’ on the top of the settings nav-bar.
- Click ‘Listen On All Interfaces’
- Click Save (bottom of the page, not show in image)
Once you’ve done this, the Pi-Hole software will process requests from Wireguard clients.
But we now have one final step - to tell your Wireguard clients to use the Pi-Hole. Open up your Wireguard client configuration (the .conf file you made in the tutorial for your phone/computer), and change one last thing:
[Interface]
...
DNS = [Pi hole IP address here]
This should be the local IP address of the Pi-Hole on your home network, on the
Wireguard interface. This should be whatever is in the Address field of your
Wireguard configuration file on your server (but without the slash). So if your
server configuration has:
...
Address = 192.168.2.1/24
...
You’d use 192.168.2.1.
Save your config file, start Wireguard, and the ads should be gone!
You’re done, you’ve finally defeated ads. Good job.
Epilogue: I can’t connect to my local network resources when I’m on WiFi?
If you don’t need this section, ignore it - be free and happy. If you notice that sometimes, when using Wireguard, you’re able to connect to your VPN server, you can browse the web, but you can’t access something on your local home network, like a NAS, or a webcam, let’s talk about IP address conflicts. Briefly. (Look, this is a complex topic, and you’ve earned your rest, but this bit me, so, since it might help someone…)
Also, we’re only going to discuss this for Windows, though a lot of the same theory may apply to other operating systems.
Anyway, you might find sometimes a local network address that worked perfectly fine on your phone, or at home, doesn’t work when you’re at a friend’s home, or at a small store with free WiFi.
This is likely an IP address conflict.
Let’s say your on your VPN, and you want to access your web camera, which has an
IP address on your local network of 192.168.1.12 on your home network. So, you
plug that in, and nothing loads. But you’re connected to Wireguard. Everything
looks like it should work. But it doesn’t.
What’s probably happening is your friend’s WiFi, or the coffee shop, or whatever
WiFi you’re on, uses the same address range as your network at home. So your
computer sees “oh, the user is trying to connect to 192.168.1.12, and I’m
currently assigned the address 192.168.1.100 - well I’m on the same subnet, so
I’ll just send this directly to that IP address and not go through the Wireguard
system.
Wireguard, however, is clever. And wants to prevent you from sending data that’s not going through Wireguard. So, it blocks the connection.
What we need to do is tell the computer “hey, when I navigate to 192.168.1.12,
I want you to go through the VPN no matter what, even if there’s already a
device, on this network, with that exact IP address. Welcome to the wonderful
world of manual routing.
You can see how Windows is routing connections - open a terminal (type
powershell into your start menu), and type route print.
There’s an excellent tutorial on HowTo Geek, but, here’s the incredibly short version: we need to tell Windows to route over the Wireguard channel. To do this, follow the tutorial, but when you get the step about adding a static route, what you’ll enter will be something like this:
route ADD [Client Wireguard IP Address] MASK 255.255.255.255 [IP Address of your NAS/Camera/etc]
Here, Client Wireguard IP is the IP address you’ve told Wireguard to assign to
this device (the Wireguard application, on Windows, will show you this when you’re
connected, under “Addresses”) - leave off any slash.
OK - that, hopefully should be everything. For real. Good night, and rest easy for you have defeated ads, and made your network safer.